
![]()
If you want an effective and different approach to computer platform security, turn to theQubes OS.
Be prepared to adjust your expectations and your computing comfort zone, however. The Qubes OS does not work the way other Linux distros work in adding extra layers of security.
It is based on the Fedora Linux desktop but goes well beyond Fedora’s approach. The Qubes OS is a hybrid computing technology that raises the bar for security.
Designed around the concept of security by isolation, it achieves that goal by using domains implemented as lightweightXen virtual machines.
Its Poland-based Invisible Things Lab development team combines two concepts. One is making the isolation between domains as strong as possible. The second is making the isolation seamless through an innovative architecture that minimizes the amount of trusted code. [*Correction – April 19, 2016]
Developers released version 3.1 last month. Qubes OS installs from a DVD but has no live session as a testing vehicle. You can try an alpha version that installs to a USB drive, but that download is an earlier version of Qubes OS.
Still, it gives you a chance to try it before you do a hard disk installation. Installing Qubes in a virtual machine rarely works. If you succeed, the performance is radically impacted. The built-in Xen hypervisor does not play nicely with the other VM environment.
Supreme Isolationism
Qubes locks down each part of the OS by compartmentalizing it. Each component of the OS is relegated to a domain structure that is isolated from all other domains.
The concept is a bit strange to grasp until you see it in operation. You can have multiple domains running on the desktop at the same time. They appear on the screen as windows running applications in a traditional Linux desktop.
The applications actually are running in separate VM windows within the Qubes OS. The barriers between domains are rigidly enforced — even performing copy and paste operations from one domain window to another requires menu-driven procedures and authorizations.
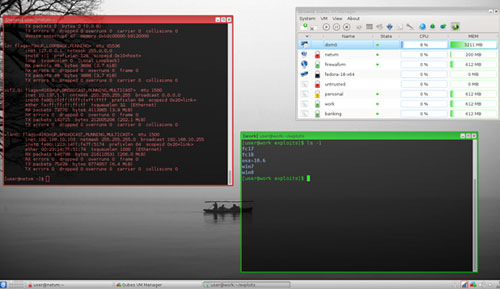
This security barrier concept ensures that rogue code or other harmful intrusions in one domain do not affect any other component in the Qubes OS. A self-destructing domain brings an added security option.
Self-Destructing Security
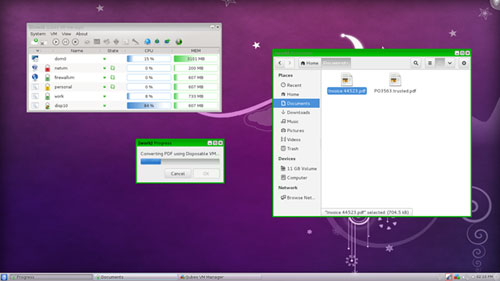
If you open a disposable domain, whatever you run and whatever data you generate from apps within it cease to exist when you close that domain.
For example, if you open a Web browser in a disposable domain and stumble on an infected website, the foreign substance would be deleted automatically when the domain closed.
Suppose you save a website to a bookmark. That bookmark and all of the history entries you visited during that browsing session are gone when you open the Web browser in another domain or a new disposable domain.
Domain Sovereignty
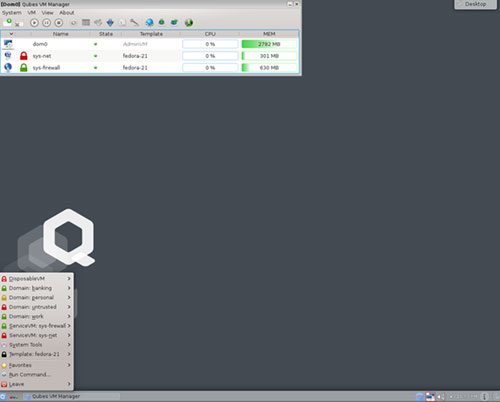
When you install Qubes OS, the process creates three default domains: work, personal and untrusted. You can create more domains using the trusted window manager.
Each domain has a name and an assigned color that functions as a label. The trusted window manager uses these colors to draw color frames around the windows border for each application running in each domain.
Dom0 is sort of a system domain separate from the default domains and any other domains you create. The desktop manager runs in this domain. Your login credentials reside there. Much like a super domain, Dom0 is more trusted than any other domain.
It is also cut off from the rest of the Internet world. Dom0 has no network connectivity. It provides just two functions: It runs the window manager and the desktop manager.
Why It Works
The Qubes OS goes beyond the limitations of the traditional monolithic OS structure. In traditional Linux operating systems, all the applications run within a single operating system. Running a distro in a virtual machine relies on using a single hosted hypervisor that creates and runs the VM environment.
The Qubes OS uses a bare-metal hypervisor called Xen. It does not run inside an existing OS. The Xen hypervisor runs directly on the bare metal of the hardware. Qubes runs compartmentalized and isolated VMs, all managed as an integrated OS.
Linux distros running in live sessions still have some vulnerabilities. VM hypervisors running on top of the host OS are only as secure as the host OS itself, according to the developers. Qubes OS’s compartmentalized Xen VMs make it much more difficult to compromise.
Using It
It took me awhile to get used to the blended user interface that drives the Qubes OS. Applications run in domain windows. Much of the desktop overlay and familiarity of the KDE and Xfce appearance exist.
However, launching programs is done differently. You control the entire Qubes system with either command line tools run under a Dom0 console or with an intuitive graphical user interface tool.
To open a console window in Dom0, go to Start/System Tools/Konsole, or press Alt + F2 and type “konsole.” Once the Qubes VM Manager is running, you can open the window at any time by clicking on the Qubes tray icon, which typically resides in the bottom-right corner of the screen.
Launching the program from the VM Manager’s menu first opens its domain window. You can open programs in an already opened domain using the menu button present in each domain window. Applications also can start from the command line.
Tricky Requirements
The hardware needs are a bit more tricky with Qubes OS. Expect roadblocks with hardware support. That can be an issue since you will not know how your hardware handles Qubes OS until after you install it.
It might help to check the Qubeshardware compatibility list. You can install the Qubes OS on systems that do not meet the recommended requirements, the developers noted. Provided the hardware is compatible, you will benefit from significant security improvements over traditional operating systems. Features such as GUI isolation and kernel protection do not require special hardware.
You’ll need a 64-bit CPU that supports virtualization technology. That support includes both Intel VT-x (or AMD-V) and Intel VT-d (or IOMMU), plus a BIOS with TPM (for Anti Evil Maid). Running numerous VMs within Qubes OS is resource-intensive, so you’ll need an abundance of RAM (4 GB is minimum) and a fast processor.
Beware Bugaboos
Macs are not supported. Their keyboard and mouse functions cause problems.
Be aware of two other hardware cautions: Nvidia GPUs may require heavy troubleshooting, and ATI GPUs have not been formally tested.
The installer loads Xen at the beginning of the installation routine. If you see the installer’s graphical screen early in the boot up, Qubes OS will probably work on your system, according to the developers.
Bottom Line
This latest version features a new management system that centrally controls the Qubes OS configuration based onSalt management software.
The in-house installation wizard offers various options to precreate some useful configurations. The release also supports booting on machines with UEFI and introduces additional hardware support for a range of video cards.
Qubes OS is not for the faint-hearted. Even Linux users familiar with other security-enhanced distros will feel the challenge in installing and setting up this unique Linux desktop.
Want to Suggest a Review?
Is there a Linux software application or distro you’d like to suggest for review? Something you love or would like to get to know?
Pleaseemail your ideas to me, and I’ll consider them for a future Linux Picks and Pans column.
And use the Talkback feature below to add your comments!
*ECT News Network editor’s note – April 19, 2016: Our original published version of this story incorrectly stated that the Invisible Things Lab is based in the U.S. It is located in Poland.





















































Nice article.
AFAIK the Invisible Things Lab development team is Poland-based. Do you have any reason to suspect otherwise?