
Online and Internet security are not topics that typical computer users easily comprehend. All too often, Linux users put their blind trust in a particular distribution and assume that all Linux OSes are equally secure.
However, not all Linux distros are created with the same degree of attention to security and privacy control. A misconfiguration of a firewall or misapplied Web browser privacy and modem settings can trash the best-designed Linux safety strategies.
Kodachi Linux offers an alternative to leaving your computer privacy and security to chance. It is developed by Oman-based Eagle Eye Digital Solutions, an IT firm with a focus on preserving computer privacy and anonymity.
The developers announced the release of Linux Kodachi 5.6 last month. Based on Debian 9.5 Xbuntu 18.04 Long-Term Support, it runs from a DVD or USB thumb drive as a live session OS for a completely isolated and secure Linux session on any computer for portable Linux convenience.
You also can install Kodachi on a hard drive. That method blunts one of the primary features of the distro, though. Running in a live session removes all traces of your Internet activity and your documents from the host computer when you remove the DVD or USB.
Otherwise, either option provides an anti-forensic, anonymous operating system with all the features a person concerned about privacy needs. In this sense, Kodachi gives you built-in techniques, gadgets, and software designed to hamper a computer investigation seeking to intercept your email or breach your digital data.
Two new features in this latest Kodachi release add additional layers of security and anonymity. One lets you self-destruct the entire computing platform with a single click. The other brings the ability to have persistent memory to live sessions so that application settings, software changes, and saved personal files remain available for subsequent computing sessions.
Easy Smeazy and Secure
Kodachi Linux requires no setup or Linux knowledge. The developer built all of the controls and settings options into the OS. The entire OS is functional from temporary memory RAM when running in the preferred live session.
Once you power off the computer in a live session, no trace is left behind. All your activities are wiped out. That is a major drawback of running Kodachi Linux as a full installation on a hard drive.
Firewalls, virtual private networks (VPNs), network nodes, and proxy servers are the technical stuff that controls your online privacy and computer security. They are also the techniques that computer users without IT training often ignore.
Kodachi Linux comes with a toolbox of security applications and an assortment of preconfigured scripts. They make using security and privacy strategies a point-and-click process.
I am by no means a formally trained IT expert. I know my way around Linux. I learned what I know from years of using it and countless hours taking seminars and reading manuals.
I spent a few hours getting familiar with this distro’s documentation and viewing online demonstrations of earlier Kodachi releases. Then I burned a DVD of the latest ISO and started to check out Kodachi hands-on.
One of the first things I did was scroll through the inventory of security tools and specialized browsers. I loaded a few system apps and took the Kodachi browser online. Then I loaded the Kodachi Security Test, which invited me to learn how to increase my security score.
It scanned the running live session for the system and Internet connections. Each component of the short “test” added or subtracted points based on how it affected the security and privacy potential of the settings.
My results? A score of 90 out of 100. This “test” offered brief explanations for what made each setting choice bad, good, or ideal. So following the recommendations would help any new user to quickly harden the security and privacy results.
How It Works
One of the hallmarks of Kodachi is its collection of specialized system and security tools. These tools and scripts are easy to modify by changing settings and editing configuration files. Of course, these are advanced skills that may take you time to acquire.
Until you do, use Kodachi out of the box. Follow the recommendations of the Security Test app’s evaluation. Use the default Kodachi Web browser. Activate Kodachi’s built-in VPN.
When you run the Kodachi browser by itself, you are not connected to the Tor network automatically. When you want to run Tor, click the grayed circle in the top row of icons in the browser’s toolbar, scroll down the service options, and select Tor. The circle turns green to indicate a Tor connection.
Browse through the VPN and Tor Tools folders and try out the various settings for other VPNs and Tor nodes. These tools mask your true IP Address, DNS provider, and real country identification.
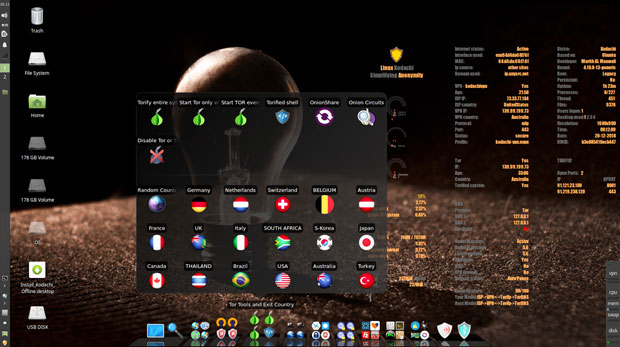
It is as simple as clicking on an icon to change settings. It takes a few seconds for the new connection to establish. Look at the screen applets to monitor the results.
Making a Recovery
If you start to make system changes and things go seriously wrong, just click on the self-healing options in the Panic Room folder. They can save you the hassle of rebooting into another live session or having to reinstall Kodachi to the hard drive.
The various tools restore the default configurations and software drivers to let you resume working in the OS without having to isolate the cause or do a system restart. It addresses problems with menu glitches, non-working hardware, or misconfigured security connections.
Overall, Kodachi is very easy to use. Whether booting from a hard drive, USB, or DVD, you have a fully running operating system with secure VPN connections plus Tor connections with DNScrypt service running.
Doubled-Down Debian
Kodachi is built around several essential design standards. One ensures privacy. Unless you disable one or more settings, all Internet connections are forced through a VPN as well as the Tor network with DNS encryption.
A second design premise is the use of state-of-the-art cryptographic and privacy tools to encrypt your files, emails, and instant messaging. Kodachi’s security is bolstered by its stable Debian base with a heavily customized Xfce desktop environment.
Kodachi supports proxy servers, but the developer cautions users to avoid the proxy feature in most Kodachi use cases. It will defeat the purpose of using Kodachi, according to EEDS CEO Warith Al Maawali, developer of the system, in a video discussing the distro’s technology.
Proxy servers are unnecessary, with the other security features in the OS with Tor activated. Proxy is included for when it is absolutely needed. The only safe strategy is to use a proxy connection when the URL you want to reach does not have a Tor or a VPN connection, Al Maawaii explained.
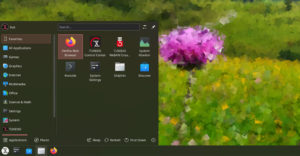
Desktop Tour
Kodachi Linux’s look and feel heavily conceals its Xfce desktop roots. The basic functionality remains. The appearance is heavily altered.
The desktop has four design elements. The left edge of the screen is bordered by a vertical panel. To the right of this panel is a vertically aligned row of icons for attached drives and folders.
The bottom of the screen sports a Cairo dock populated with a collection of folders containing application launchers. The launch icons rise and enlarge as the mouse pointer floats over them.
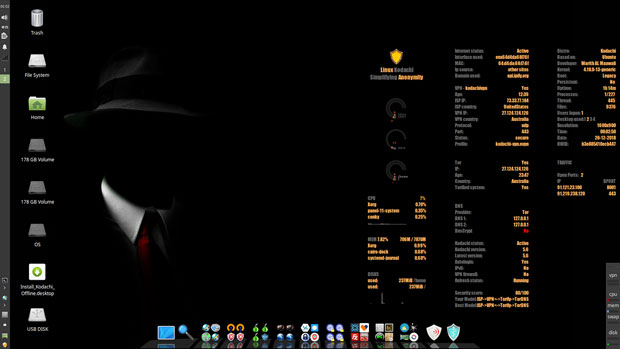
The right side of the desktop displays several applets and readouts. They monitor system status and Internet connection details.
Desktop Layout
The left panel retains the configurability of the standard Xfce panel. You can select user preferences and add/remove panel applets.
The top end of the vertical panel holds the usual system notification symbols. The lower end holds launchers for a few system tools.
The launcher button for the Main menu is at the bottom or first position of the vertical panel. The menu display is a single-column panel in the lower-left corner of the screen with a cascading sub-panel. The categories are what you would expect elsewhere, except for the addition of a Security category.
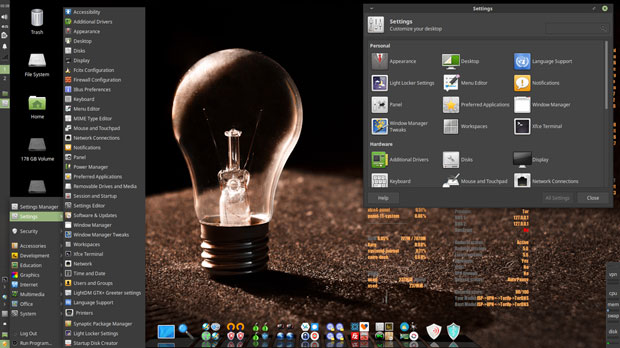
You get a limited selection of background images but do not expect any colorful, cheery scenes. The images are largely colorless and highlighted with dark tones.
Also included is the classic right-click system menu that pops up anywhere on the desktop. However, you can not dock application icons on the Cairo dock, the desktop itself, or the left panel bar. Nor is there a favorites display for frequently used programs.
Software Supreme
A key strength of Kodachi Linux is the inclusion of multiple tools for the same task. For instance, you get multiple shells — Torrified Shell, Terminator Window, and Root Terminator.
Kodachi Linux is more than a well-tuned specialty distro for security and privacy. It also is a very capable computing platform for everyday personal and business tasks.
It has the Synaptic Package Manager preinstalled for system maintenance and software addition/removal. However, so much software is included that unless you have unique needs, nothing should be missing from the default installation.
That says something about the overall quality and usefulness of this distro. I am not suggesting that the developers are guilty of pushing software bloat. Given that its primary purpose is to run as a live session, the large bundle of included software is unusual without first completing a hard drive installation.
The applications are high-quality open-source titles. Included are LibreOffice, Blender, Inkscape, Audacity, OpenShot Video Editor, and lots more.
Browsers Galore
Kodachi comes with several specialized Web browsers. The default Web browser is the Kodachi Security Browser. It is the Firefox browser with a library of plugins to enhance security and privacy. The toolbar has numerous buttons to activate security and proxy services.
By design, the Google Chrome browser is not included for obvious reasons. Chrome is embedded with tracking and data harvesting services that defy Kodachi’s goal of enhanced Internet security and privacy. The browsers use the Duck Duck Go search servers instead of Google search services.
Firefox Direct VPN Browser is included. So is Waterfox Direct VPN Browser. Waterfox is forked from Firefox and maintains support for legacy extensions dropped by Firefox.
The Iridium browser is another choice. Iridium is based on the Chromium code base. Its modifications enhance user privacy with security technologies.
Bottom Line
By default, the system uses DNS-Crypt. You can change that with one click to more rigorous encryption by clicking on the icon for Tor-DNS in the DNS Tools folder on the bottom dock.
The security toolset lets you test the speed of each VPN connection as well as the relative security. You also can check for DNS leaks as part of the security reliability of each connection.
The DNS, VPN, and Security Tools folders on the bottom dock are arranged in rows, usually with five icons across stacked three rows high. The position of the icon within the multi-row mapping indicates how each tool compares with the others. Their positions are in ranked order based on the developer’s performance and reliability assessments.
So the tools in the bottom row are less secure than the middle row. The top-row tools are the most secure. The same hierarchy plays out from left to right in each row. The left side is less secure than the right side.
Suggest a Review
Is there a Linux software application or distro you’d like to suggest for review? Something you love or would like to get to know?
Email your ideas to me, and I’ll consider them for a future column.
And use the Reader Comments feature below to provide your input!





















































A review of Linux Kodachi 8.27 in 2023!
Linux Kodachi 8.27 continues to impress with its focus on privacy and security. As someone who works in IT for RACV and has an affinity for technology, this distribution might be of particular interest to you. The latest version maintains its reputation for providing a secure and anonymous computing environment, making it a solid choice for individuals who value their online privacy.
One of the standout features of Linux Kodachi is its emphasis on anonymity. With tools like the built-in VPN and Tor integration, you can browse the internet with confidence, knowing that your online activities are shielded from prying eyes. This is especially relevant given your background in IT and your work with RACV, where cybersecurity is undoubtedly a priority.
The integration of gardening and swimming into your personal interests might not directly relate to Linux Kodachi, but it’s worth mentioning that this distribution allows you to focus on your hobbies without worrying about online vulnerabilities. Whether you’re researching gardening tips or planning a swimming excursion, you can do so with the assurance that your online identity is protected.
In terms of performance, Linux Kodachi 8.27 maintains its reputation for being lightweight and efficient. This is crucial for users who appreciate a smooth computing experience, whether they’re using it for work-related tasks or leisure activities like gardening and swimming.
However, as with any operating system, there are always areas for improvement. While Linux Kodachi excels in privacy and security, users might find the learning curve a bit steep if they’re not familiar with Linux-based systems. It’s always a good idea to provide thorough documentation or tutorials for newcomers to help them navigate the system more easily.
In conclusion, Linux Kodachi 8.27 remains a solid choice for privacy-conscious users in 2023. Its focus on anonymity aligns well with your background in IT and your appreciation for gardening and swimming, allowing you to enjoy your hobbies without compromising your online security. As the digital landscape continues to evolve, having an operating system that prioritizes privacy is more important than ever.
Great article. I just recently discovered Kodachi and I must say I am impressed with the level of security that it presented me and also all the preloaded software, Tor connection and even more impressed that my MAC address was changed automatically. Things that normally would take me some time in other distros, Kodachi did it as it loaded.
Now, my question to you is, I know that Installing it on a hard drive defeats the purpose of anonymity, however for overall security and considering how robust this system is, don’t you think it is a good idea to install it? for daily use, I rather use this distro rather than using Mint or any other distro with Tor and VPN, etc etc. I rather install this on my HD and forget about anything else.
Whats your take on that????
Thanks for your comments. I fully agree with your assessment. All the other security features Kodachi offers remain available with a full disk installation. The odds are still in your favor for better security control than you have with many other Linux options.
Best wishes,
Jack M. Germain
LinuxInsider