
![]()
Linux users are blessed with a collection of file encryption tools. But chances are, whatever application you use for that task lacks the efficiency, speed and functionality of TrueCrypt.
TrueCrypt does what any file encryption application is supposed to: It locks down access to your data so no one without a password or keyfile can grab it. But the process TrueCrypt employs and its toolkit of features separates this file encryption product from other contenders.
It stores your data on an encrypted volume that lets you work seamlessly. This on-the-fly access automatically encrypts the data before it is saved and decrypts when the file loads. Unlike other encryption programs, you do not have to click or drag files to interact with the process.
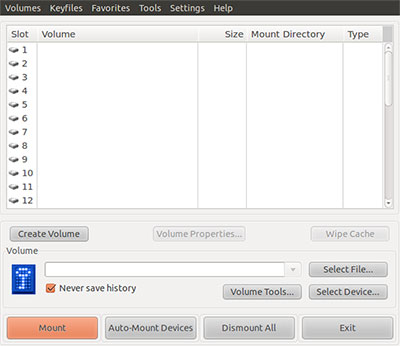
Another essential difference with TrueCrypt is the level of security it brings to your data. This application controls the entire file system. It encrypts everything from file and folder names to the contents of every file. This encryption locker even includes the volume’s free space and metadata.
Getting It
Despite how easy it is to work with TrueCrypt, installing it can be a little bothersome. In my case, the standard compressed download file was useless on my Ubuntu 10.10 installation. I had the same problem with another desktop running Ubuntu 11.04 .
I unarchived the tarball file I downloaded from the developer’s site. Then I clicked on the resulting executable file as per the directions provided.
That seemed to install TrueCrypt. The installation process planted an entry in the Accessories menu. But TrueCrypt failed to run when I selected it.
First-time users should open a setup wizard. Until TrueCrypt creates its storage volume, the rest of the program is inaccessible. So nothing happened.
Fixing It
The fix for this SNAFU was simple enough to do. But it should have been offered as a download option from the developer’s site to avoid my having to hunt down a solution.
I found a .deb file for TrueCrypt here. The .deb format is a native file package format that works on Debian-based Linux distros. Ubuntu is a Debian derivative.
Once I downloaded the .deb installation file and clicked on it, the Ubuntu package manager cleanly installed it. Clicking on the menu entry then ran the set-up wizard as it should.
Make sure that you have the current version, however. The latest stable version is 7.0a released on Sept. 6, 2010.
Next Steps
TrueCrypt offers some options on setting up the storage media. You can create an encrypted volume in a file, a partition a drive. You also have the option to create a standard or hidden encrypted volume to store your data.
Think of the TrueCrypt storage container as a file. You can place it anywhere, such as the hard drive, an external hard drive or large-capacity USB drive or other external media. Just as you can do with a regular file, you can move it, copy it or even delete it.
Use the location selector window in the GUI (Graphical User Interface) to complete your choices. Once you complete these steps, the file selector window disappears.
Almost Gotcha
Be careful when you select a file name and location. I almost walked into a minefield of errors when navigating through the set-up wizard.
TrueCrypt does not encrypt any existing files when it first creates its file container. If you goof and select an existing file during the setup’s naming process, you will overwrite it. That, of course, doesn’t encrypt the data — instead, it wipes that data out.
Not to worry, though. Just be sure you use a unique name for the TrueCrypt volume. Later in the process you can encrypt existing files by moving them to the newly-created TrueCrypt volume.
Big Tip: After copying existing unencrypted files to the TrueCrypt volume, securely wipe the original unencrypted files. To do this, you will need another tool. But again, Linux offers ample options.
Secret Sauce
TrueCrypt is loaded with features. Perhaps the most important choices in using this encryption application are selecting the degree and type of encryption. The setup wizard asks you to choose an encryption algorithm and a hash algorithm for the volume.
I chose the default settings. My work is not rocket science, so I am comfortable with default security levels.
The next decision involves setting the size of the TrueCrypt container. Ample help is available in the on-screen prompts to guide you.
An equally critical decision is setting your password. Again, read the documentation provided to prep yourself about what makes a strong password. Then apply those tips to creating a rock-solid password to protect your encrypted data.
Engage Encryption
My initial reaction to this next final setup step was mild amusement. I’m glad that I did not fully ignore the importance of establishing the cryptographic strength of the encryption keys. Making light of this final setup step would have greatly weakened the effectiveness of TrueCrypt’s security.
This process involves randomly moving the mouse randomly about within the Volume Creation Wizard window for at least 30 seconds. Move it around even longer to create a more secure encryption.
Clicking the Format button begins the volume creation process. When it is finished, you will see a new file or volume created in the location you specified earlier in the set-up routine. Do not forget to click the Mount button so you can use the encrypted volume.
Bottom Line
TrueCrypt is an ideal way to place your critical data files in a virtually impenetrable sealed crypt. The encryption process only requires an entry password. Once entered, file operations work in and out of the virtual storage disk much like with a physical disk.
No room for error exists. TrueCrypt handles file encryption and file-saving chores. Even if I forget to unmount the encrypted file or volume, updated content in temporary memory is encrypted and moves to its iron-clad storage vault when the operating system shuts down.




















































Is TrueCrypt only for Linux users? Doesn’t seem like its meant for a commercial audience. It reminds me of the MyLOK, by ii2p.com, as far as general functionality. But I would like to see something for non-Linux users.
In court I mean? I know the whole thing about TrueCrypt is "plausible deniability" but has anyone ever tested that in court? I know in the UK they can force you to give up your keys, and they threw a guy here in the USA in jail for refusing to give the keys to his laptop, so has anyone court tested this?
You see the thing that worries me about software and claims like TrueCrypt is there is geek logic and then there is court logic, and rarely do the two meet. So I’d love to hear from anyone that has any info on court cases involving TrueCrypt as i’d love to see what the laws say about it with regards to keys and privacy.
Thanks for an informative article Jack.
You may like to know that installing the 64-bit tarball from the developer’s site and installing it on my Ubuntu 11.04 system on AMD worked fine. So, I’m not sure what the problem might have been with your installation.
Thanks again.