‘Tis the season to go phishing. Nothing brings out digital bandits like the holidays, and this year is no exception.
Proofpoint, an enterprise digital security company, reported Tuesday its researchers are seeing a massive global increase in holiday-themed mobile phishing attacks, a.k.a. smishing.
It noted the volume of mobile phishing messages has almost doubled, compared to this time last year.
Those messages are promising everything from package and gift deliveries to special retail offers and special delivery exceptions.
“There has been a trend the past few years of scams and smishing related to the holidays and holiday themes in the fourth quarter of the year,” observed Jacinta Tobin, Proofpoint’s global vice president of Cloudmark operations.
“We have seen steady growth both from our U.S. and global scam and smishing reports starting in October and increasing through December,” she told TechNewsWorld.
Season of Susceptibility
Ben Brigida, director of SOC operations at Expel, a SOC-as-a-Service provider in Herndon, Va. explained that phishing attacks increase during the holidays because people are more susceptible to social engineering targeting their desire to show their loved ones they care.
“It’s not unusual to get advertisements promising great deals around this time, or to have someone ask if you want to chip in on a large gift,” he told TechNewsWorld.
“Attackers can send an email about a deal that’s too good to be true for the hot new toy and people will fall for it,” he said.
“They can impersonate a manager,” he continued, “and ask for someone to ‘pick up gift cards for everyone in the office’ and it actually makes sense, so people do it.”
Magni R. Sigurdsson, senior manager of detection technologies at Cyren, a cybersecurity company in McLean, Va. that focuses on protecting businesses from phishing attacks and data loss, noted that SMS phishing campaigns have increased because there are more mobile users and devices than there were a year ago.
“Phishing is a commercial enterprise, so cybercriminals adapt to changes in consumer behaviors just as legitimate businesses do,” he told TechNewsWorld.
High Click-Rate Success
“As consumers rely more on mobile devices, it’s only natural that attackers will focus on those platforms,” observed John Bambenek, principal threat hunter at Netenrich, a San Jose, Calif.-based IT and digital security operations company
“That’s especially true considering that the click rate on SMS attacks is so much higher than on emails and the fact that there is relatively far less security on mobile devices,” he told TechNewsWorld.
“So attacks have absolutely increased, and they will continue to do so,” he said.
Hank Schless, senior manager for security solutions at Lookout, a San Francisco-based provider of mobile phishing solutions, noted there were significant increases in enterprise mobile phishing at the end of both 2019 and 2020. From Q4 2019 to Q1 2020, volume increased 87 percent, while from Q4 2020 to Q1 2021, they jumped 127 percent.
“The interesting thing is that from that point forward in 2021, threat actors didn’t relent and the encounter rates continued to increase through the first three quarters of 2021, showing that this is a significant problem that’s here to stay,” he told TechNewsWorld.
Bogus Customer Service
In a Proofpoint blog, Tobin wrote that cybercriminals prey on mobile users with smishing attacks that claim to be from reputable companies, including prominent retailers, e-commerce brands, and parcel delivery companies.
These lures attempt to steal personal information from unsuspecting targets, she added.
Many of these lures request credit card information to resolve an issue supposedly related to the purchase or delivery of a nonexistent item, she noted.
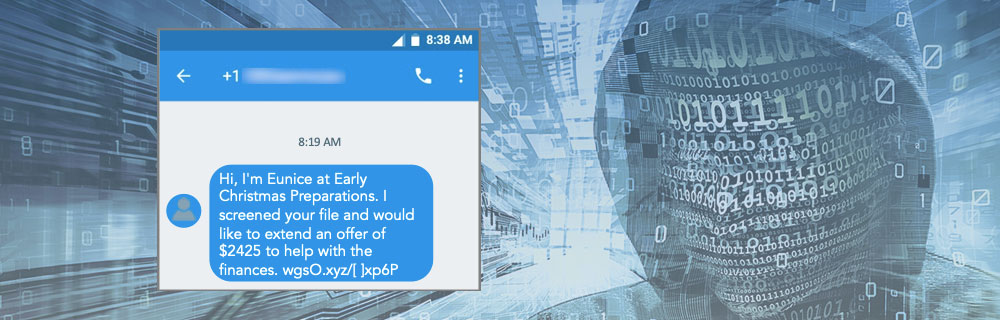
Example of a fraudulent SMS notification attempting to steal personal information (Image Credit: Proofpoint)
In other cases, she wrote, the attackers attempt to steal personal information through an enticing URL or landing page.
Expel has seen similar activity online. In a blog item posted Monday, it called out a shipping scam where a target was notified about the purchase of a high ticket item they hadn’t bought.
There are no clickable links in the email — just a phone number for a “support desk” printed in bright red type at the bottom of the purchase notification.
When the notification’s recipient calls the phone number, a “customer service rep” offers to clear up the problem, after collecting the necessary account information to sort out the problem.
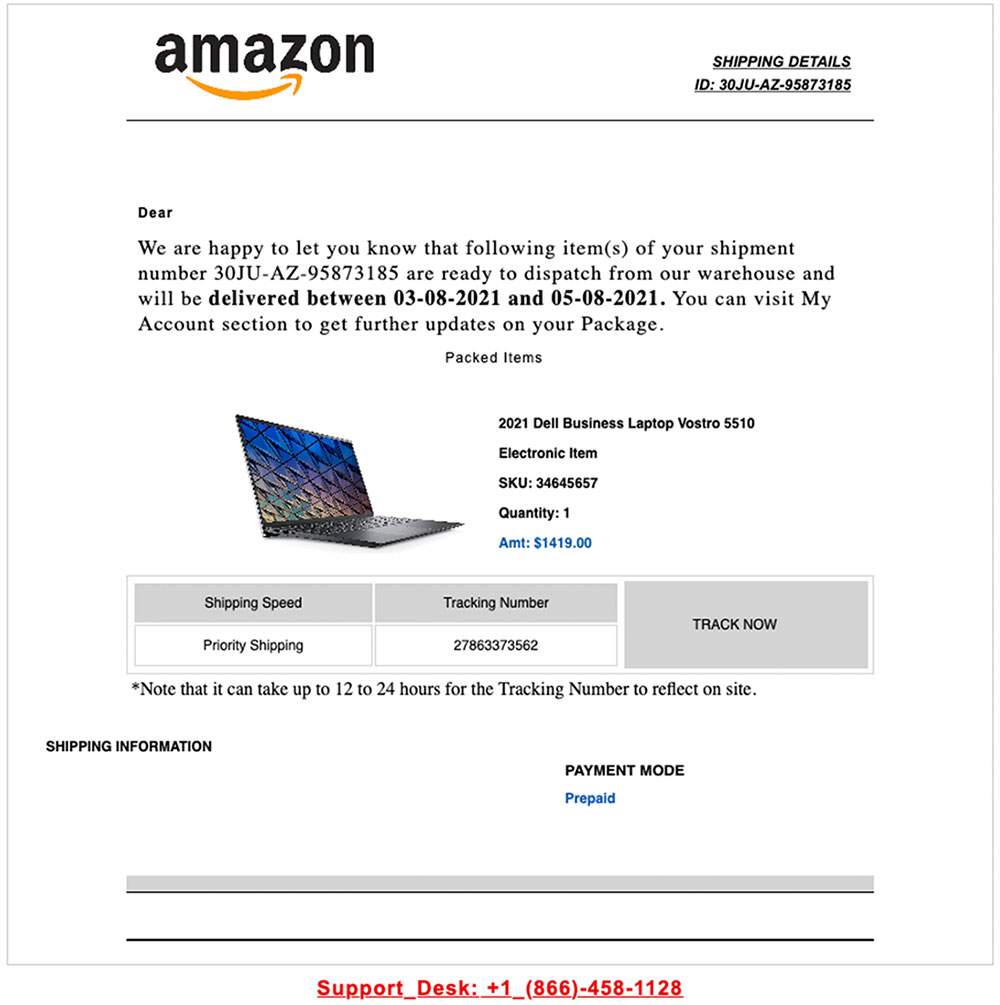
Example of a fake Amazon shipping notification email (Image Credit: Expel)
If successful, this type of scam would result in the attacker obtaining account credentials, credit card numbers, or other sensitive personal information from the concerned recipient, Expel explained.
“The uptick in consumer purchases during the holiday season provides an abundance of opportunities for attackers to dupe people into disclosing sensitive information,” observed Expel Security Operations Manager Ray Pugh.
“Fake purchase receipts, invoices, and shipping notifications are particularly likely to prompt recipients to click links or call phone numbers listed in the phishing email, given recipients are expecting these types of emails at this time of year, so the call to action is strong and attackers’ odds of success are especially high during the holidays,” he told TechNewsWorld.
Precautionary Measures
In her blog, Tobin offered some advice for mobile safety during the holidays.
- Be on the lookout for suspicious text messages. Criminals increasingly employ mobile messaging and SMS phishing as an attack vector.
- Be cautious about providing your mobile phone number to an enterprise or other commercial entity.
- Whenever you receive a message, including some sort of warning or package delivery notification that contains a web link, do not use the web link provided in the text message. Instead, use your device’s browser to access the sender’s website directly, or use the brand’s app, if you already have it installed on your device. Do this as well for any offer codes you receive by entering them directly into the sender’s website from your browser.
- Report SMS phishing and spam to the Spam Reporting Service. Use the spam reporting feature in your messaging client if it has one, or forward spam text messages to 7726, which spells “SPAM” on the phone keypad.
- Be careful about downloading and installing new software to your mobile device. Read install prompts closely, particularly for information regarding rights and privileges that the app may request.
- Don’t respond to any unsolicited enterprise or commercial messages from any vendor or enterprise you don’t recognize. Doing so will often confirm that you’re a “real person.
- Don’t install software on your mobile device from any source other than a certified app store from the vendor or Mobile Network Operator.
- “Consumers should realize that SMS messages are more insecure than email and that every message they receive is suspect,” Bambenek said.
“They should prefer app-based messaging as opposed to text,” he added, “and to realize that if something is too good to be true it probably is.”













































