Internet security researchers at Eset on Tuesday published a security research paper on Linux/Moose, a major threat to social networks that turns routers into conduits for grabbing users’ log-in credentials, employing them for network fraud and to further spread malware to client devices that connect through them to the Internet.
The paper, “Dissecting Linux/Moose,” details a months-long investigation into a carefully concealed flow of traffic involving the malware and recommends how to avoid prolonged exposure to it.
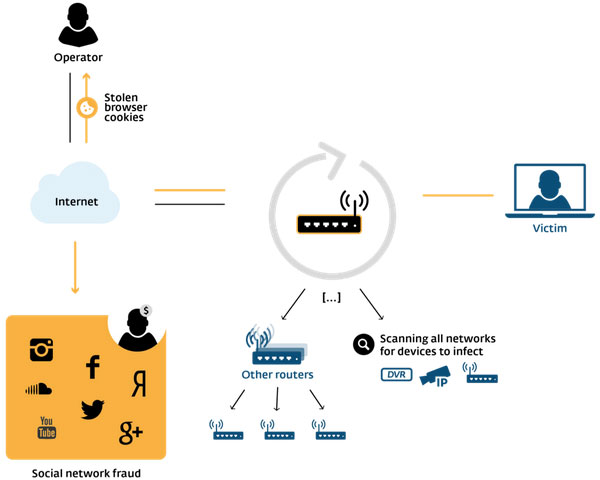
Linux/Moose is a worm that primarily targets Linux-based cable and DSL modems, as well as home routers and other Linux-based embedded systems. Once infected, the compromised devices are used to steal unencrypted network traffic and offer proxying services for the botnet operators.
Linux/Moose allows cybercriminals to skim unencrypted information about users’ social media accounts that then can be used to sign up those individuals as social media followers for people and businesses that pay for followers, according to James Quin, senior director of content & C-suite communities atCDM Media.
“As with virtually all security hacks these days, this is all about money,” he told LinuxInsider. “It’s fraud being perpetrated on the people that pay for the follows, giving them followers that don’t want to follow them.”
Moose Tracks
Eset researchers Olivier Bilodeau and Thomas Dupuy named the malware after a file named “elan2” that they found within the coding. The word “elan” is French for “moose.”
The researchers first detected the malware activity last July. Moose’s main purpose appears to be creating a network of covert HTTP proxies used by the worm’s command- and-control servers to communicate with social networks.
Their account does a pretty good job of summarizing both how to remove the problem and how to protect against it. Unfortunately, most people will not know what to do with the information, noted CDM Media’s Quin.
“It is going to be beyond the technical sophistication of the vast majority of people that could be impacted since the threat targets consumer grade equipment, and the resolution it requires involves logging into the administrative console,” he said.
What It Does
Hackers use Linux/Moose to steal HTTP cookies in order to perform fraudulent actions on Facebook, Twitter, Instagram, YouTube and other social sites. The goal is to generate non-legitimate “follows,” “views” and “likes.”
Linux/Moose is a novelty, because most embedded threats today perform DDoS attacks, according to Eset’s Bilodeau. This one produces a false revenue stream using people’s social media accounts.
“The ultimate goal of this malware would seem to be the proliferation of bogus social media accounts. Often these kinds of accounts are used for click-fraud, social media spam, survey scams and malware,” said Brad Cyprus, chief of security and compliance atNetsurion.
By deploying Moose, the botnet operator gets clean IP addresses of home routers. That makes it easy for hackers to start creating accounts. From there comes the profit, noted Tom O’Connor, Linux solution expert at Raytheon Cyber Products.
Packs More Threat Potential
This type of malware also can reroute DNS traffic, enabling man-in-the-middle attacks across the Internet. Linux/Moose displays out-of-the-ordinary network penetration capabilities, compared to other router-based malware.
Moose also has DNS hijacking capabilities and will kill the processes of other malware families competing for the limited resources offered by the infected embedded system.
Wireless routers are an ideal target for cybercriminals. When attackers gain control of a router, they can monitor, redirect, block or otherwise tamper with a wide range of online activities, said Craig Young, security researcher at Tripwire.
“I recently compiled research that revealed 80 percent of Amazon’s top 25 best-selling Small Office/Home Office wireless router models have security vulnerabilities,” he told LinuxInsider. “Plus, 34 percent of the 50 top-selling models have publicly documented exploits that make it relatively simple for attackers to target vulnerable systems.”
Not Just a Linux Thing
Linux has not been plagued by security problems any more than any other operating system, per se. It is just that cybercriminals are targeting systems that they know have poor security, noted Quin.
“Linux ends up being the target, because the open source operating system ends up being used in huge numbers of low-cost devices that are sold to people that really don’t have the technical acumen to make them secure,” he said.
“The fact that it is Linux is more of a coincidence than actual targeting, and if these devices used Windows as their baseline operating system, we’d be remarking on the preponderance of Windows breaches,” Quin added.
In fact, Linux’s success is making it more of a target. It is not caused by its vulnerability, said Netsurion’s Cyprus.
“As Linux becomes more pervasive in powering the Internet of things, it becomes ever more attractive and viable as an attack target. Also, the proliferation of open source applications and components means they are subject to a high level of scrutiny and attack now,” he told LinuxInsider.
With the current Moose implementation, no Linux-specific security vulnerability is being exploited. Poor credentials are to blame, Raytheon’s O’Connor told LinuxInsider.
“More and more SOHO routers are running embedded Linux, rather than other proprietary, less well-known operating systems. The explosion of popularity of Linux, and its ability to run on laptops, servers, Android phones, IoT devices and SOHO routers, makes it a much more attractive target than it was in years past. With that popularity, comes more attention — both positive and, in this case, negative,” he said.
How It Works
Moose exploits routers open to connections from the Internet via Telnet by performing brute-force login attempts using default or common administrative credentials. Once connected, the worm installs itself on the targeted device.
Moose spreads using a file named “elan2.” Once installed, the malware monitors Web traffic passing through the router to detect unencrypted cookies in Web browsers and mobile applications. It then passes the information to unencrypted sites that leverage social network features.
Its attack capabilities include intrusions into Twitter, Facebook, Instagram, Google, Google Play/Android and Youtube using stolen logons.
The Moose worm uses rudimentary techniques to gain access to other devices. Vendors generally do not take seriously the security of embedded devices, but Eset’s analysis can help them to better understand how the malicious actors are targeting their devices, report author Oliver Bilodeau suggested.
Linux/Moose may not be able to stay on a router or other embedded computing devices, according to Netsurion’s Cyprus. Once the router is powered off, it restarts without the worm present.
“Users can defend against this malware by rebooting their router, changing the default password of the router so the hackers cannot get back in and infect the router again, and updating the firmware of the router so that the vulnerability is addressed if the manufacturer has already released a patch for this issue,” he advised.
Caveat Included
Poorly configured routers that are reset could quickly be reinfected by other compromised routers or devices on the local network, notes the Eset report.
Moose may not be targeting Internet of Things devices by design, but Eset researchers found that itcould infect a number of them, including medical equipment.
For example, medical devices like the Hospira Drug Infusion Pump could be infected with Linux/Moose, according to the report.
Moose encrypts its data delivery using HTTPS, but researchers traced the destination sites and linked a connection between the traffic and fraudulent social media accounts, Bilodeau explained.
The proxy service is created on TCP port 2318 on the router’s Internet network interface. It takes incoming Web requests from a whitelisted set of IP addresses and redirects them as HTTPS requests to social media sites.
Prevent and Fix
Users can defend against Linux/Moose by changing the default credentials for their broadband routers, said Trend Micro Global Threat Communications Manager Christopher Budd.
Even if they are not running a router that could be affected by this malware, it is still a smart best practice, he told LinuxInsider.
To minimize wireless attacks, Tripwire’s Young offered several tips: First, do not enable remote management over the Internet. Second, do not use the default IP ranges. Rather than 192.168.1.1, consider 10.9.8.7 or something else that is not commonly used.
Third, never forget to log out after configuring the router. Also, turn on encryption and turn off WPS. Turning on AES-backed WPA2 protected with a strong (26+ character) preshared key is ideal.
Also, remember that passwords matter. Default passwords are often the same for an entire product line or are generated from a common algorithm, making a device easy prey for an attacker. It is imperative that you change passwords rather than using defaults.
Finally, keep the router firmware up-to-date. That will fix known product issues, including security problems.