In what might belong in the “better late than never” category, the U.S. government and the computing industry are ramping up efforts to deal with seemingly runaway cybersecurity issues.
On Friday, the Department of Homeland Security announced that its Cyber Safety Review Board (CSRB) will conduct a review on cloud security involving the malicious targeting of cloud environments.
The initiative will focus on providing recommendations for government, industry, and cloud services providers (CSPs) to improve identity management and authentication in the cloud.
Initial efforts will review last month’s Microsoft cloud hack in which researchers found that Chinese hackers forged authentication tokens using a stolen Azure Active Directory enterprise signing key to break into M365 email inboxes. The hack led to the theft of emails from approximately 25 organizations.
The board will then expand to issues involved with cloud-based identity and authentication infrastructure affecting applicable CSPs and their customers. This part of the review may have even more widespread significance in fixing broken cybersecurity processes.
US Enhances Cloud Security Measures
The CSRB’s role is to assess significant incidents and ecosystem vulnerabilities and make recommendations based on the lessons learned. According to government officials, the board brings together the best expertise from industry and government.
“The Board’s findings and recommendations from this assessment will advance cybersecurity practices across cloud environments and ensure that we can collectively maintain trust in these critical systems,” offered Cybersecurity and Infrastructure Security Agency (CISA) Director Jen Easterly.
In a related announcement on Aug. 8, the National Institute of Standards and Technology (NIST) released a draft of an expanded cybersecurity framework version 1.0 it first introduced in 2014. Cybersecurity Framework (CSF) 2.0 is the first revision of the cybersecurity assessment tool since then.
After considering more than a year’s worth of community feedback, NIST released the new draft version of the Cybersecurity Framework (CSF) 2.0 to help organizations understand, reduce, and communicate about cybersecurity risk. It reflects changes in the cybersecurity landscape and makes it easier to implement the cybersecurity framework for all organizations.
“With this update, we are trying to reflect current usage of the Cybersecurity Framework and to anticipate future usage as well,” said NIST’s Cherilyn Pascoe, the framework’s lead developer.
“The CSF was developed for critical infrastructure like the banking and energy industries, but it has proved useful everywhere, from schools and small businesses to local and foreign governments. We want to make sure that it is a tool that’s useful to all sectors, not just those designated as critical,” she added.
Dovetailing Earlier Cyber-Safety Strategies
The White House on Thursday opened a request for information for public comment on open-source software security and memory-safe programming languages.
The goal is to build on its commitment to invest in developing secure software and software development techniques. The request for public comment also seeks to advance initiative 4.1.2 of the National Cybersecurity Strategy Implementation Plan the White House released to secure the foundation of the internet.
The White House on July 13 issued the National Cybersecurity Strategy Implementation Plan (“NCSIP”). It identifies 65 initiatives led by 18 different departments and agencies designed as a roadmap for implementing the U.S. National Cybersecurity Strategy it released in March.
Responses are due by 5:00 p.m. EDT on October 9, 2023. For information on submitting comments, see the Fact Sheet: Office of the National Cyber Director Requests Public Comment on Open-Source Software Security and Memory Safe Programming Language.
Microsoft Response May Set Precedent
According to Claude Mandy, chief evangelist for data security at Symmetry Systems, the above-referenced Microsoft cloud breach highlighted two issues.
First, it revealed how Microsoft’s commercial constructs bundle needed security features with other products. The intent is to restrict customers from selecting competitive products on a commercial basis, he said.
That restricts companies from having essential security features without paying for more than what is needed. In this case, it involves logs in the authentication process, according to Mandy.
The second revelation is that details on how the breach occurred and what potential impact and data could be impacted are still vague, with no certainty provided by Microsoft, Mandy proffered. That happened despite the focus and investment from Microsoft on cybersecurity as a revenue stream.
“As an industry, we are demanding more transparency,” he told TechNewsWorld.
The most significant lesson from this breach for organizations, he noted, is that logging and monitoring of data events — or data detection and response — is the biggest lever that one has in the cloud to detect, investigate, and respond to security incidents, particularly those involving third parties.
“Most interesting in the short term from this review will be how far the precedent that Microsoft has set in committing to provide these logs at zero cost will be adopted or enforced upon other cloud service providers,” he said.
Half of Cloud Security Faults Ignored
The Qualys Threat Research Unit analyzed the state of cloud security and released findings earlier this month.
Researchers discovered that misconfigurations in cloud security providers provided ample opportunities for threat actors to target organizations, especially when combined with externally facing vulnerabilities that remained exposed and put organizations at risk, according to Travis Smith, VP – Threat Research Unit at Qualys.
“Across the three major cloud security providers, configuration settings designed to harden cloud architectures and workloads were only enabled correctly roughly 50% of the time. On a similar note, 50.85% of externally facing vulnerabilities remain unpatched,” he told TechNewsWorld.
While a review will provide visibility into the risks of moving computing resources to the cloud, it does not appear that organizations are heeding that warning, Smith confided.
That finding does not bode well for better cybersecurity. The researchers’ first review focused on vulnerabilities in Log4J. Cyber experts are seeing that Log4Shell is still widely prevalent in cloud environments, with patches found 30% of the time, he offered.
No Solution for Key-Based Cloud Security
Key-based security will always have this breaching problem. There is always, in some sense, a master key, one key to rule them all, suggested Krishna Vishnubhotla, VP of product strategy at Zimperium. So just choosing robust cryptographic algorithms and schemes is not enough.
“The more significant concern is protecting the keys from being exfiltrated and abused. Keeping keys secure is not a sound practice in most enterprises,” he told TechNewsWorld.
Multicloud and hybrid cloud are pervasive throughout the enterprise, from computing to authentication. Therefore, the master key represents access to all enterprise systems.
“Whether enterprises should entrust their master keys to Cloud Providers or if the enterprises should take on this responsibility is the real question,” he suggested.
New Cybersecurity Framework Holds Promise
Efforts to update security recommendations could be an uphill battle beyond actual cyber experts. One of the perennial problems in cybersecurity is how to talk about security to leadership and the board quantitatively, offered John Bambenek, principal threat hunter at Netenrich.
“Expanding these frameworks to all organizations and not just critical infrastructure opens the door to being able to do so in a consistent way across the economy and hopefully will lead to more buy-in of using security to reduce business risk,” he told TechNewsWorld.
The addition of a sixth function, “govern,” is a clear message to organizations that to be successful, there also must be actively managed policies and processes underpinning the other functional areas, praised Viakoo CEO Bud Broomhead.
For example, governance should ensure that all systems are visible and operational and that enterprise-level security processes and policies are in place.
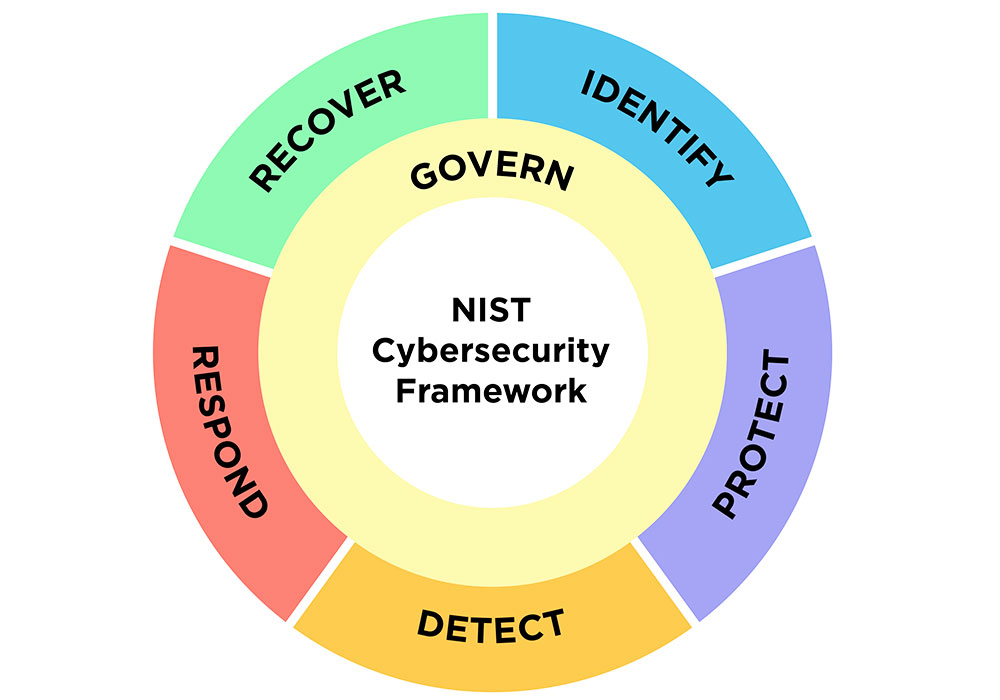
To the five main pillars of a successful cybersecurity program, NIST has added a sixth, the “govern” function, which emphasizes that cybersecurity is a major source of enterprise risk and a consideration for senior leadership. (Credit: N. Hanacek/NIST)
Expanding the scope of the NIST framework to all forms of organizations, not just critical infrastructure, acknowledges how every organization faces cyber threats and needs to have a plan in place for managing cyber hygiene and incident response, Broomhead explained.
“This is already the case with cyber insurance, and NIST’s recent update will help organizations not just reduce their threat landscape but also be better positioned for compliance, audit, and insurance requirements on cybersecurity,” he told TechNewsWorld.
Step in the Right Direction
NIST’s update should also push more organizations to work with managed service providers on their cyber hygiene and cybersecurity governance, Broomhead urged.
Given that NIST expands its scope to include smaller organizations, many will find that a managed service provider is the best way to make their organization compliant with the NIST Cybersecurity Framework v2.0.
The latest update to the Cybersecurity Framework is an excellent refresh of one of the best cybersecurity risk frameworks, offered Joseph Carson, chief security scientist and advisory CISO at Delinea.
“It’s great to see the framework moving on from simply a focus of critical infrastructure organizations and adapting to cybersecurity threats by providing guidance to all sectors,” he told TechNewsWorld.
“This includes the new govern pillar acknowledging the changes in the way organizations now respond to threats to support their overall cybersecurity strategy.”























































