
A family of Linux malware targeting Linux and BSD servers has been lurking around for five years, Eset has reported.
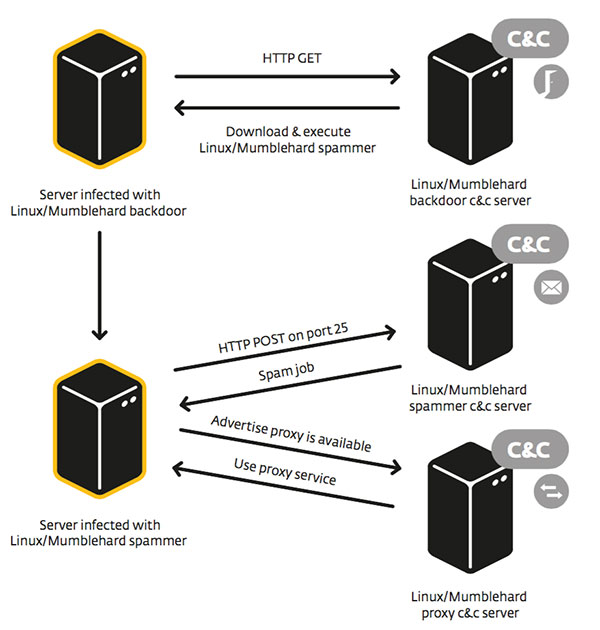
Dubbed “Linux/Mumblehard,” the malware contains a backdoor and a spamming daemon, both written in Perl.
The components are mainly Perl scripts encrypted and packed inside an executable and linkable format, or ELF, said Eset. In some cases, one ELF executable with a packer nests inside another.
An Eset sinkhole saw more than 8,800 unique IP addresses over seven months. Web servers are the most susceptible to the attack.
Mumblehard is strongly linked to YellSoft, a Russian online company that sells bulk email software.
“The severity of Mumblehard is paramount because of the complexity of the malware, widespread nature of the infection, and indication of high intent from the hackers to exploit these systems,” Secure Channels CEO Richard Blech told LinuxInsider.
Mumblehard’s Methods
Writing ELF binaries in assembly language obfuscates the Perl source code and shows an above-average level of sophistication, Eset noted.
Mumblehard’s main purpose appears to be sending pharmaceutical spam from legitimate servers it takes over.
The attacks appear to come in waves. The number of hosts infected by Mumblehard is decreasing, but infections occur at specific times, and the botnet has doubled in size over a six-month period, Eset pointed out. The highest number of unique IP addresses hitting Eset’s sinkhole in one day was about 3,300.
Mumblehard probably spreads in one of two ways, Eset suggested. One is through Joomla and WordPress exploits.
The other is through pirated copies of the DirectMailer software package, which runs on Linux and BSD and is available on YellSoft’s Website for US$240. They have a Perl backdoor that installs in crontab, asks C&C servers every 15 minutes for commands, and reports whether it’s successful or not.
The backdoor supports only one command, “download from URL and execute.”
There are 10 C&C servers in the DirectMailer list, only one of which sends commands, and Eset speculates that the others might be blinds.
Mumblehard also could run on Windows.
The DarkMailer Discussion
Yellsoft’s DirectMailer spamware is also known as “DarkMailer.” It apparently can be identified on Unix or Linux systems by doing a process status.
Any Web server that can run Perl scripts, including Windows, Unix, Linux and FreeBSD, and that lets users, customers or even admins change their Web pages, is a potential victim.
Is Open Source Unsafe?
Many Linux administrators have expressed the notion that open source systems are more secure than other operating systems. However, that claim is untrue, said Secure Channels’ Blech.
“It’s more a question of an uptick in publicity,” suggested Bill Weinberg, senior director of open source strategy at Black Duck Software.
Of the 8,000 to 10,000 vulnerabilities detected across IT annually, “around 40 percent are in open source,” he told LinuxInsider.
Open source theoretically has a security advantage, as it is subject to the scrutiny of more eyes than proprietary software, but all scrutiny is not equal, Weinberg observed.
The open software model allows overlapping scrutiny — first by developers, then by platform creators such as Red Hat, then by end users including OEMs, enterprise IT staff and consumers, he explained. The further you get from the core developers, the less familiarity there is with the source code — and, therefore, the less the likelihood of flaws being spotted.
Protecting Against Mumblehard
To fend off Mumblehard, administrators of Linux systems can encrypt their data, Blech suggested.
A whiteboxing technique that bars malware from elevating its permissions and running discovery to find system information is effective, he said. Even if information is found, it’s returned as ciphertext, which is useless to hackers.
IT staff should look for unsolicited cronjob entries for all the users on their servers, Eset suggested. The Mumblehard backdoor usually is installed in /tmp or /var/tmp, and mounting the tmp directory with the “noexec” option prevents the backdoor from executing.




















































